Microsoft Releases May 2023 Patch Tuesday Updates for Windows 11 and Windows 10

Microsoft has just released the May 2023 Patch Tuesday updates for Windows 11 and Windows 10. This month, Microsoft fixed a total of 38 security flaws in Windows and other components, and there are seven critical vulnerabilities in the list.
On the quality and experience updates front, Microsoft has fixed an interoperability issue between the new Windows Local Administrator Password Solution (LAPS) and legacy LAPS policies. On Windows 11 version 22H2, this update also introduces a new setting for receiving the latest non-security updates as soon as they’re available.
Let’s take a look at the most important vulnerabilities Microsoft fixed in the May 2023 Patch Tuesday updates.
38 vulnerabilities fixed in the May 2023 Patch Tuesday updates
This month, Microsoft has patched seven critical vulnerabilities, including a Windows OLE remote code execution vulnerability that has already been disclosed to the public. There’s also one Win32k elevation of privilege vulnerability labeled “important” that is already being exploited by attackers.
According to the Zero Day Initiative, this total of 38 patches is the lowest amount of fixes Microsoft released on Patch Tuesday since August 2021. Anyway, here are the main vulnerabilities you should know about:
| Product | Impact | Max Severity | Article | Download | Details |
| Microsoft SharePoint Server Subscription Edition | Spoofing | Important | 5002390 | Security Update | CVE-2023-24950 |
| Microsoft SharePoint Server 2019 | Spoofing | Important | 5002389 | Security Update | CVE-2023-24950 |
| Microsoft SharePoint Enterprise Server 2016 | Spoofing | Important | 5002397 | Security Update | CVE-2023-24950 |
| Windows 10 Version 22H2 for 32-bit Systems | Elevation of Privilege | Important | 5026361 | Security Update | CVE-2023-24949 |
| Windows 11 Version 22H2 for x64-based Systems | Elevation of Privilege | Important | 5026372 | Security Update | CVE-2023-24949 |
| Windows 11 version 21H2 for ARM64-based Systems | Elevation of Privilege | Important | 5026368 | Security Update | CVE-2023-24949 |
| Windows Server 2022 (Server Core installation) | Elevation of Privilege | Important | 5026370 | Security Update | CVE-2023-24949 |
| Windows Server 2022 (Server Core installation) | Elevation of Privilege | Important | 5026456 | Security Hotpatch Update | CVE-2023-24949 |
| Windows Server 2019 (Server Core installation) | Elevation of Privilege | Important | 5026362 | Security Update | CVE-2023-24949 |
| Windows Server 2016 (Server Core installation) | Remote Code Execution | Important | 5026363 | Security Update | CVE-2023-24947 |
| Windows Server 2012 R2 (Server Core installation) | Remote Code Execution | Critical | 5026415 | Monthly Rollup | CVE-2023-24903 |
| Windows Server 2012 R2 (Server Core installation) | Remote Code Execution | Critical | 5026409 | Security Only | CVE-2023-24903 |
| Windows Server 2012 (Server Core installation) | Remote Code Execution | Critical | 5026419 | Monthly Rollup | CVE-2023-24903 |
| Windows Server 2012 (Server Core installation) | Remote Code Execution | Critical | 5026411 | Security Only | CVE-2023-24903 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Remote Code Execution | Critical | 5026413 | Monthly Rollup | CVE-2023-24903 |
| Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) | Remote Code Execution | Critical | 5026426 | Security Only | CVE-2023-24903 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Remote Code Execution | Critical | 5026408 | Monthly Rollup | CVE-2023-24903 |
| Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) | Remote Code Execution | Critical | 5026427 | Security Only | CVE-2023-24903 |
| Windows 10 for x64-based Systems | Remote Code Execution | Critical | 5026382 | Security Update | CVE-2023-24903 |
| Microsoft Office LTSC for Mac 2021 | Remote Code Execution | Important | CVE-2023-29344 | ||
| Microsoft 365 Apps for Enterprise for 64-bit Systems | Remote Code Execution | Important | Click to Run | Security Update | CVE-2023-29344 |
| Windows Sysmon | Elevation of Privilege | Important | Information | Security Update | CVE-2023-29343 |
| Visual Studio Code | Information Disclosure | Important | Release Notes | Security Update | CVE-2023-29338 |
| Microsoft Word 2013 Service Pack 1 (64-bit editions) | Security Feature Bypass | Important | 5002365 | Security Update | CVE-2023-29335 |
| Microsoft Word 2016 (64-bit edition) | Security Feature Bypass | Important | 5002369 | Security Update | CVE-2023-29335 |
| Windows Server 2012 R2 (Server Core installation) | Security Feature Bypass | Important | 5026366 | IE Cumulative | CVE-2023-29324 |
| Microsoft Excel 2013 Service Pack 1 (64-bit editions) | Remote Code Execution | Important | 5002384 | Security Update | CVE-2023-24953 |
| Microsoft Excel 2016 (64-bit edition) | Remote Code Execution | Important | 5002386 | Security Update | CVE-2023-24953 |
| Microsoft Office Online Server | Remote Code Execution | Important | 5002372 | Security Update | CVE-2023-24953 |
Quality and experiences updates in May 2023
If you’re running the latest version of Windows 11 (version 22H2), this month’s Patch Tuesday Update adds a new option on the Windows Update page for downloading the latest optional non-security updates released at the end of every month as soon as they’re available. This toggle is disabled by default on devices managed by an organization.
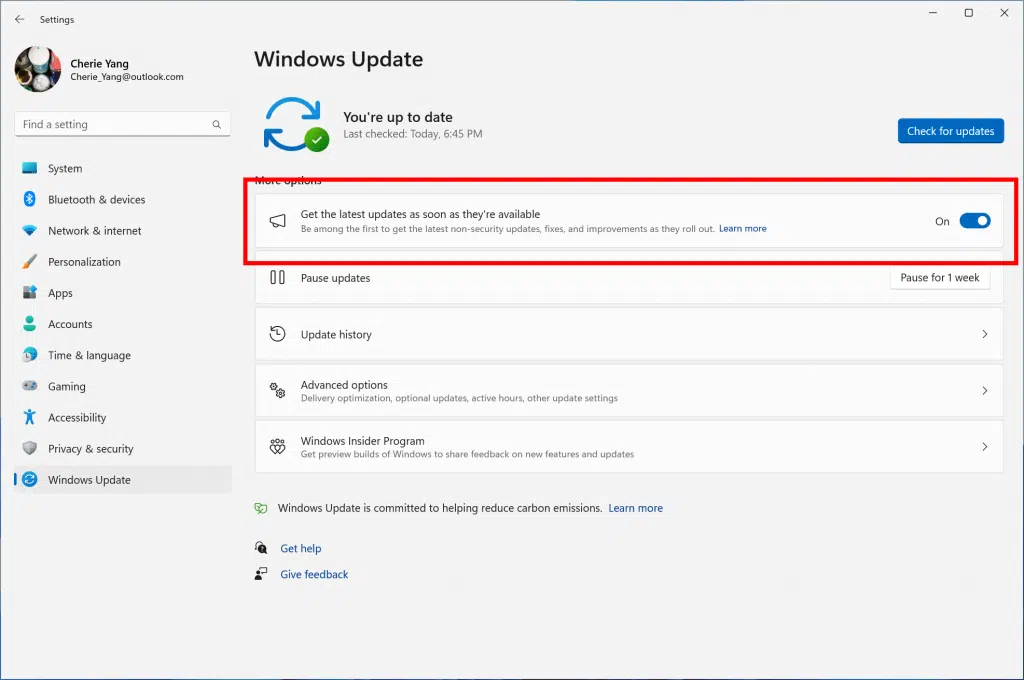
As I mentioned earlier, Microsoft has also addressed the interoperability issue between the new Windows LAPS and legacy LAPS policies. This applies to Windows 11 versions 22H2 and 21H2, as well as Windows 10 version 22H2.
This is more anecdotal, but today’s KB5026372 update for Windows 11 version 22H2 also introduces new animated icons for widgets on the taskbar. Lastly, Microsoft has also fixed an issue causing minimized windows with protected content to be visible in taskbar live thumbnail previews.
Windows Update testing and best practices
Organizations looking to deploy this month’s patches should conduct thorough testing before deploying them widely on production systems. That said, applying the patches widely shouldn’t be delayed longer than necessary as hackers start to work out how to weaponize newly reported vulnerabilities.
A best practice is to make sure you have backed up systems before applying updates. Every month, users experience issues with Windows updates that lead to systems not booting, application and hardware compatibility issues, or even data loss in extreme cases.
There are backup tools built into Windows and Windows Server that you can use to restore systems in the event a patch causes a problem. The backup features in Windows can be used to restore an entire system, or files and folders on a granular basis.
If you have any problems with this month’s patches, please let us know in the comments below. Other readers might be able to share their experiences in how to roll back problematic updates or mitigate issues caused by patches that are important to have in place.
